CSU San Bernardino has joined the ranks of eduroam campuses. We deployed eduroam in August 2012. Almost immediately we had our our first external user — from Australia no less!
We hope these configuration notes will assist in making network connectivity more streamlined for our fellow .edu folks.
- NPS: Defining RADIUS clients
- Aruba: as RADIUS client
- Cisco: as RADIUS client
- NPS: Connection Request Policy
- NPS: Network Policy
- NPS: Certificate
- Logging and Debugging
NPS RADIUS Clients and Servers
Our Aruba controllers were each defined as clients through the GUI.
We also have a large number of "fat" Cisco access points. These were originally added via netsh, although later these were replaced with one entry and a netmask.
- NPS: RADIUS clients using netmasks
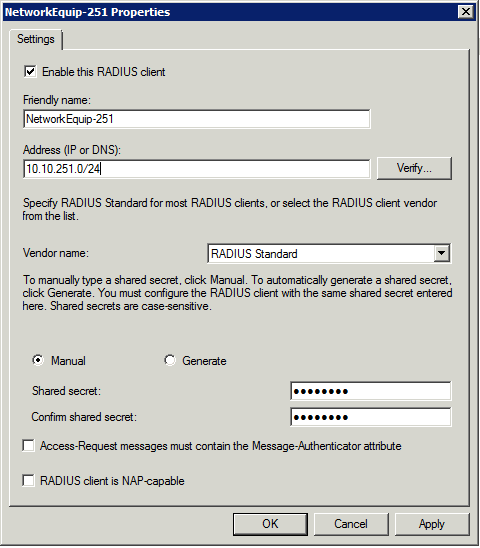
netsh nps add client cisco-ap-100-10 10.10.100.10 sharedsecret=f00b@rbaZZZ
netsh nps add client cisco-ap-100-11 10.10.100.11 sharedsecret=f00b@rbaZZZ
netsh nps add client cisco-ap-100-12 10.10.100.12 sharedsecret=f00b@rbaZZZ
…
US Top level as clients
- NPS: RADIUS clients
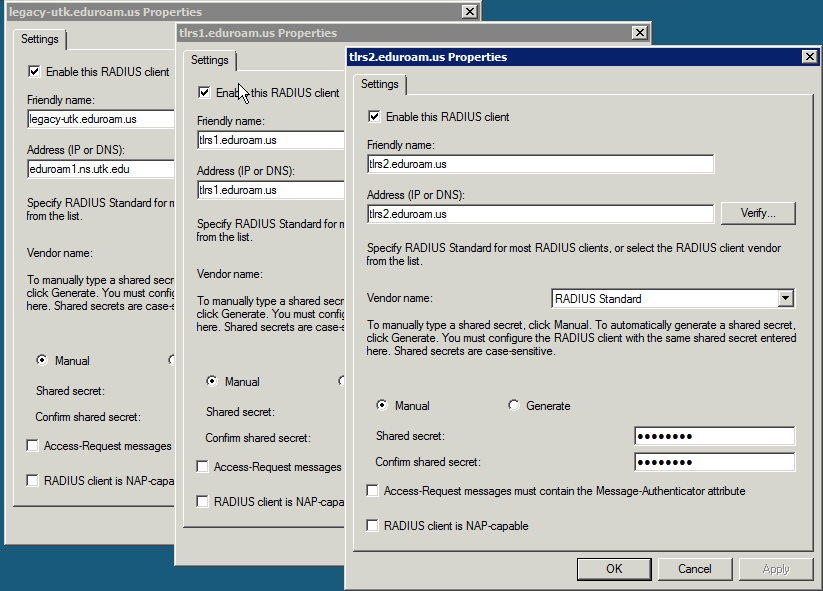
The US Top Level servers were added as documented at eduroam.us
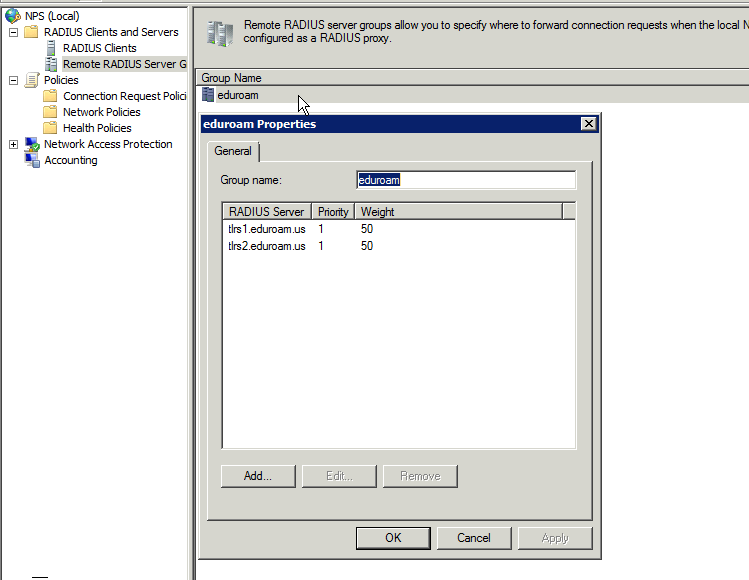
- NPS: Remote RADIUS Server Groups
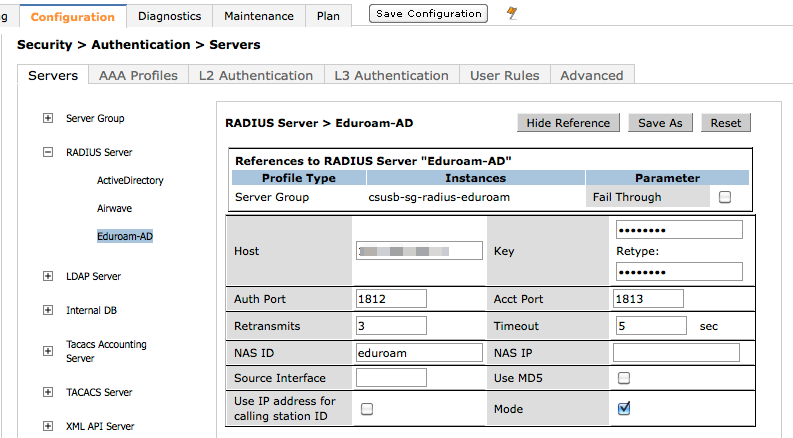
Local RADIUS clients: Aruba
On the Aruba controllers, the Radius server is defined several times. Each definition contains a different NAS ID corresponding to a different SSIDs. We had issues with special characters in the NAS ID attribute (dashes), so we do not use them.
- Aruba eduroam RADIUS server definition
- Aruba eduroam AAA profile
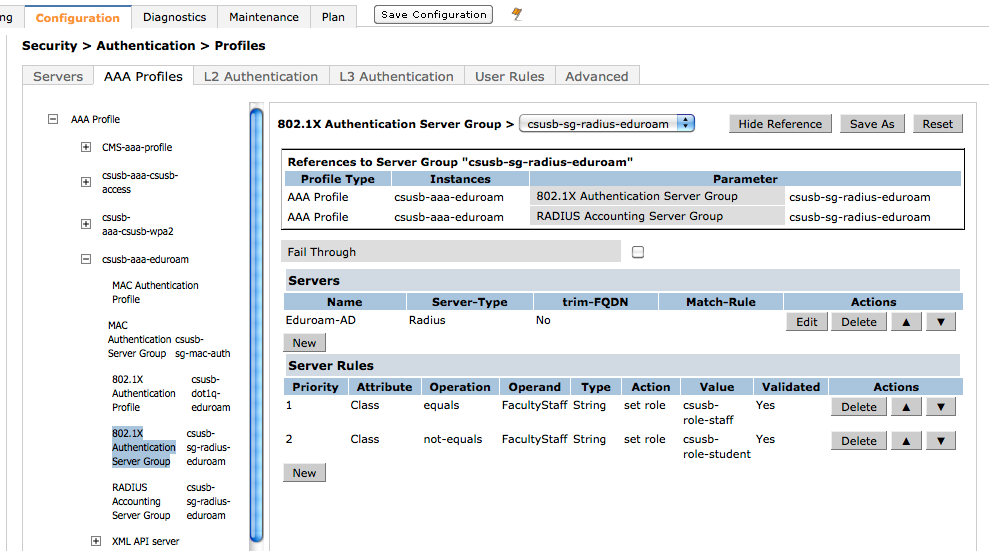
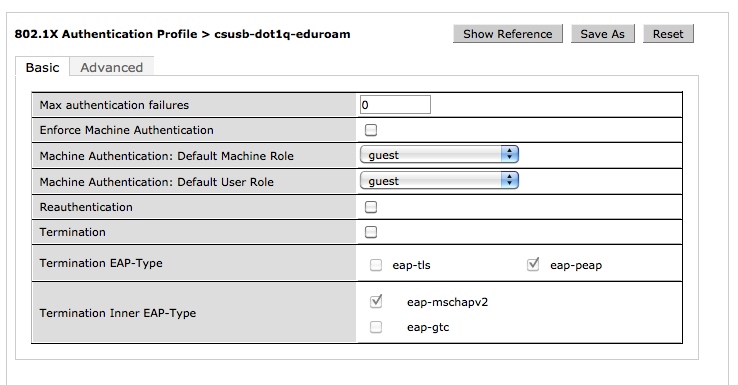
Our legacy WPA2 network is configured with EAP terminating on the Aruba controllers. However, this is incompatible with eduroam as EAP-PEAP needs to terminate at each participating institution. So, Termination is disabled (unselected) for eduroam.
- Aruba eduroam EAP - no termination
Local RADIUS clients: Cisco
The NAS ID is also known as attribute 32. We were able to set the value of the attribute using a format string.
Assuming that you already have a Cisco AP up and running on your network, these are the additional commands that need to be input for the eduroam SSID to function. Items to change are the <radius server IP>, <RADIUS key> and vlan number under SSID and sub-interfaces.
radius-server attribute 8
include-in-access-req radius-server attribute 32 include-in-access-req format eduroam
radius-server dead-criteria time 60 tries 10
radius-server host <radius server IP> auth-port 1812 acct-port 1813
radius-server retransmit 2
radius-server deadtime 15
radius-server key <radius key>
radius-server vsa send accounting
radius-server vsa send authentication
!
aaa group server radius radsrv
server <radius server IP> auth-port 1812 acct-port 1813
!
aaa authentication login eap_methods group radsrv
aaa authorization network default group radsrv
aaa accounting send stop-record authentication failure
aaa accounting session-duration ntp-adjusted
aaa accounting update newinfo periodic 15
aaa accounting exec default start-stop group radsrv
aaa accounting network default start-stop group radsrv
aaa accounting network acct_methods start-stop group radsrv
aaa accounting connection default start-stop group radsrv
aaa accounting system default start-stop group radsrv
aaa accounting resource default start-stop group radsrv
aaa nas port extended
aaa session-id unique
!
!!Be sure to add the mbssid command under your own campus SSID!!
dot11 ssid <campus SSID>
mbssid guest-mode
dot11 ssid eduroam
vlan <vlan#>
authentication open eap eap_methods
authentication network-eap eap_methods
authentication key-management wpa optional
accounting acct_methods
no guest-mode
mbssid guest-mode
!
dot11 holdoff-time 60
dot11 location isocc PT cc 351 ac 21
dot11 ids eap attempts 32 period 8
!
!
interface Dot11Radio0
!
mbssid
encryption vlan <vlan#> mode ciphers aes-ccm tkip
broadcast-key vlan <vlan#> change 600 membership-termination capability-change
!
ssid eduroam
!
countermeasure tkip hold-time 0
speed ofdm separate
dot1x reauth-period 300
!
interface Dot11Radio0.<vlan#>
encapsulation dot1Q <vlan#>
no ip route-cache bridge-group <vlan#>
bridge-group <vlan#> subscriber-loop-control
bridge-group <vlan#> port-protected
bridge-group <vlan#> block-unknown-source
no bridge-group <vlan#> source-learning
no bridge-group <vlan#> unicast-flooding
bridge-group <vlan#> spanning-disabled
!
interface FastEthernet0.<vlan#>
encapsulation dot1Q <vlan#>
no ip route-cache
bridge-group <vlan#>
no bridge-group <vlan#> source-learning
bridge-group <vlan#> spanning-disabled
!
Connection Request Policies
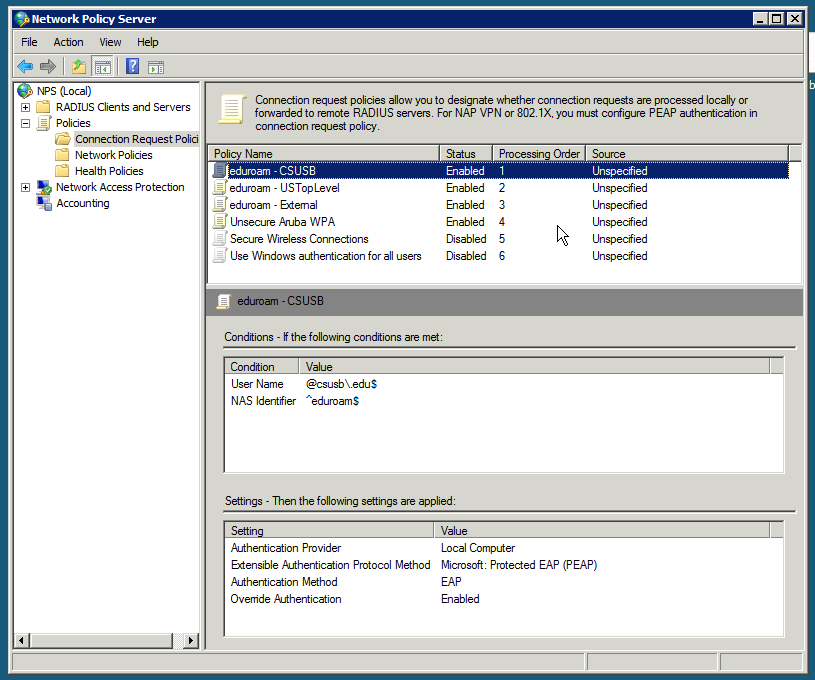
Enforcing the best practice of always requiring a realm (e.g. @csusb.edu) even for local users is done with Connection Request Policies. This is because the Microsoft NPS does not have access to the User Name attribute in Network Policies.
NAS Identifier: The NAS Identifier attribute is used internally for convenience. It is not required or used by the eduroam federation.
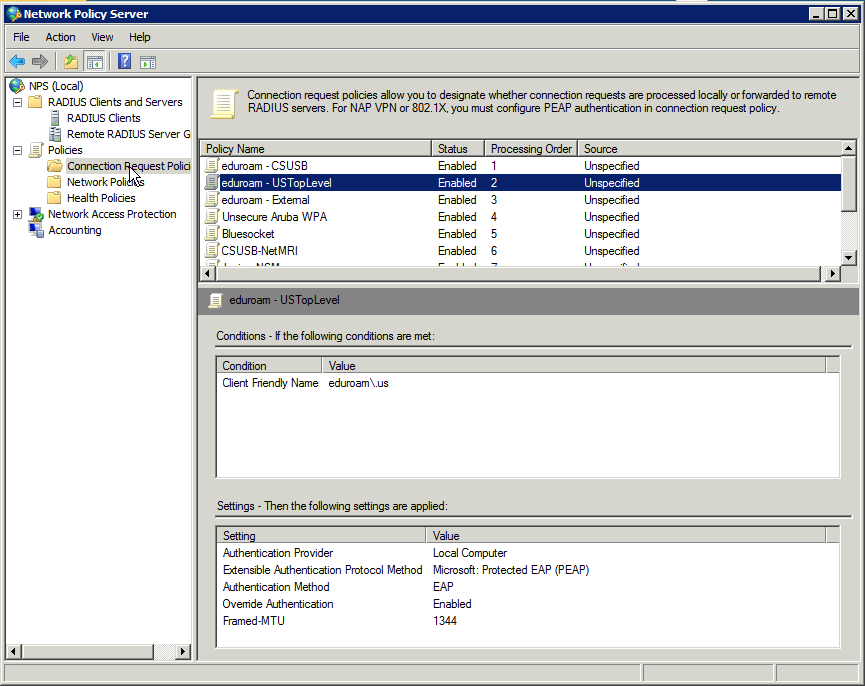
Framed-MTU: (missing from the older screenshots) After initial deployment, we also configured the Framed-MTU attribute with a value of 1344 in all eduroam Connection Request Policies and Network Policies to avoid IP Fragmentation as per eduroam-US Best Practices. Although we did observe IP Fragmentation before the configuration change, it did not seem to affect functionality.
- Connection: eduroam - CSUSB
If radius client is associated with eduroam (matching NAS Identifier), and User Name matches the regular expression@csusb\.edu$ accept PEAP-MSCHAPv2 and authenticate locally - Connection: eduroam - USTopLevel
If the radius client's friendly name matches the regular expression for eduroam\.us (forwarding from another institution) accept PEAP-MSCHAPv2 and authenticate locally - Connection: eduroam - External
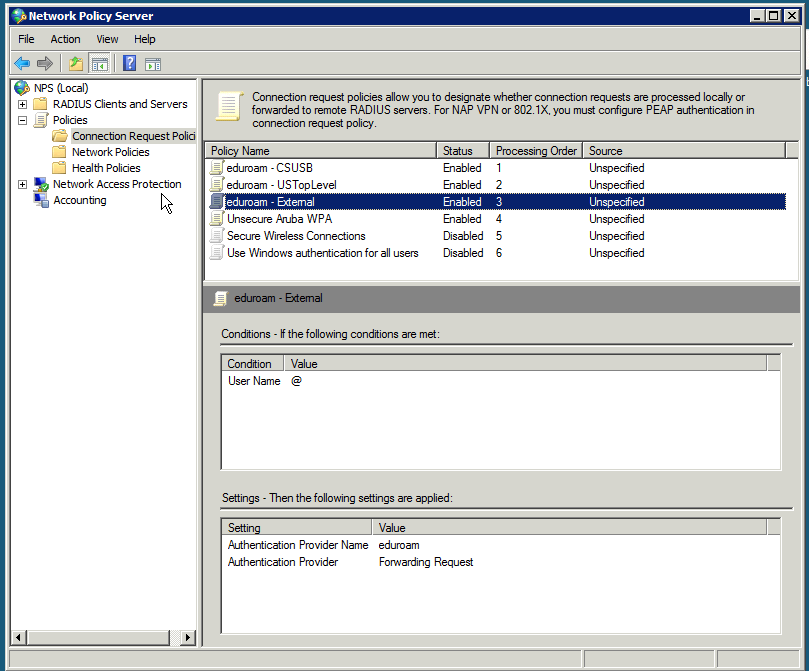
If User Name matches the regular expression @ forward to eduroam USTopLevel. This is intentionally placed aftereduroam - USTopLevelto prevent reflecting US Top Level clients back to US Top Level - If radius client is associated with other SSIDs (matching NAS Identifier) authenticate locally
- Refuse implicitly other connections (e.g. eduroam missing a realm).
Network Policies
We use network polices to explicitly drop some users. We also add RADIUS attributes help with mapping clients into various wireless roles via the Aruba controller.
- Deny Access: active accounts that don't have wireless privileges
- Policy: eduroam - CSUSB - FacultyStaff
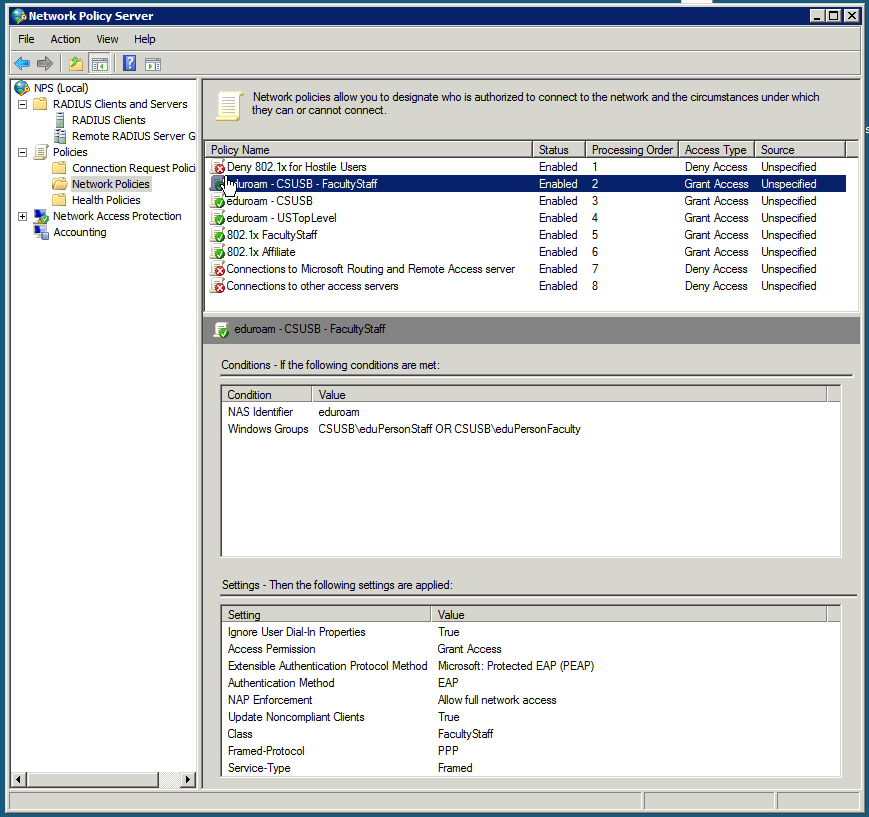
Grant Access: Add Class attribute for faculty and staff (local RADIUS clients) - Policy: eduroam - CSUSB
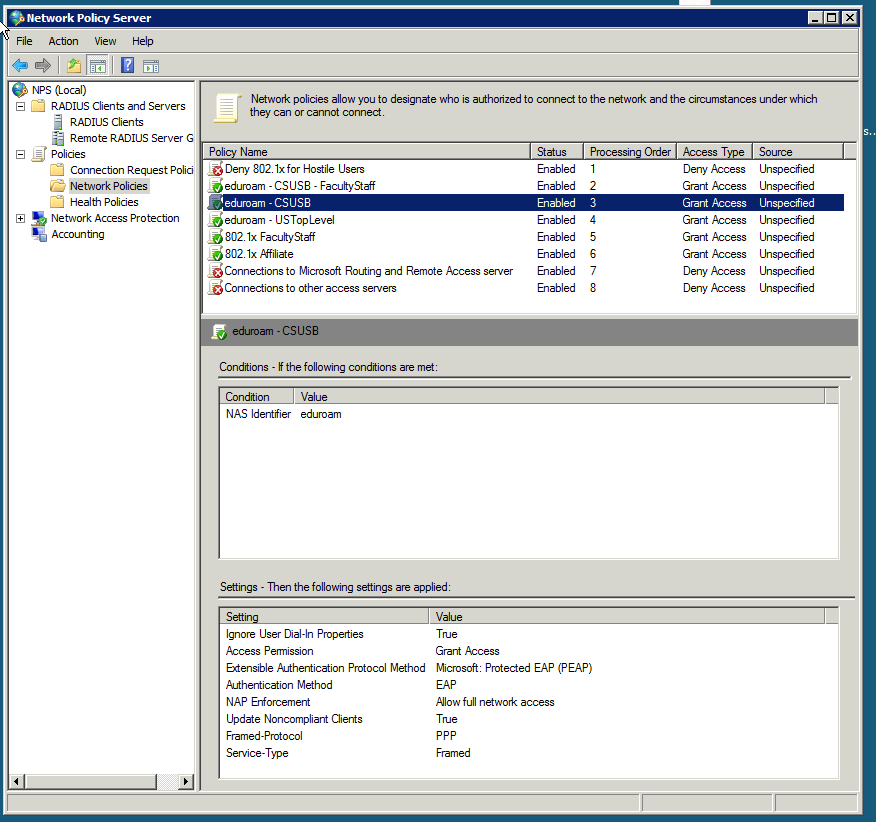
Grant Access: Omit Class attribute for students, affiliates, etc. (local RADIUS clients) - Policy: eduroam - USTopLevel
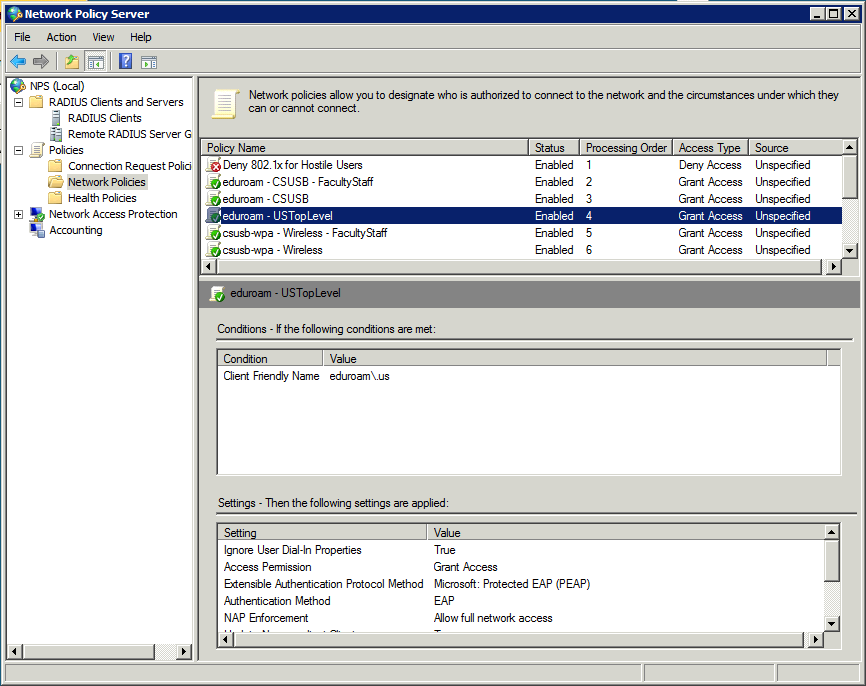
Grant Access: Remote eduroam USTopLevel RADIUS client - Grant Access: Other local legacy 802.1x RADIUS clients
- Deny Access: explicit deny
Certificate
The NAS server is configured with an InCommon certificate using the procedure in Microsoft KB 321051.
Certificate issues are difficult to debug. The Windows 7 802.1x supplicant will silently refuse to connect to Protected EAP termination points that identify themselves with untrusted certificates — "Windows was unable to connect to eduroam". Equally unhelpful, the NAS logs will just show a authentication failure.
We used a combination of MMC Certificates snap-in (Local Computer, Computer account), tcpdump/wireshark, and eapol_test to confirm the proper certificate chain, including intermediate certificates, were presented to supplicants.
Certificate: eapol_test
$ ./eapol_test -c csusb-local-account.conf \
> -N 32:s:eduroam \
> -a central.csusb.edu -s "f00b@rbaZZZ" | grep TLS
TLS: Phase2 EAP types - hexdump(len=8): 00 00 00 00 1a 00 00 00
TLS: using phase1 config options SSL: TLS Message Length: 3685
TLS: tls_verify_cb - … CN=InCommon Server CA'
TLS: tls_verify_cb - … CN=InCommon Server CA'
TLS: tls_verify_cb - … CN=central.csusb.edu'
SSL: TLS Message Length: 59
EAP-PEAP: TLS done, proceed to Phase 2
TLS: Phase 2 Request: Nak type=254
TLS: Allowed Phase2 EAP types - hexdump(len=8): 00 00 00 00 1a 00 00 00
$ cat csusb-local-account.conf
network={
ssid="eduroam"
key_mgmt=IEEE8021X
eap=PEAP
pairwise=CCMP TKIP
group=CCMP TKIP WEP104 WEP40
phase2="auth=MSCHAPV2"
identity="eduroam_testing@csusb.edu"
password="P@ssphrases R bestest!"
}
The eapol_test includes -N 32:s:eduroam to send the NAS ID attribute which will match the NPS Connection Request Policy requirement. We use grep to filter for certificate specific information. The actual output lines are much longer and truncated for clarity. We want to verify both the server certificate CN=central.csusb.edu and the chain certificate CN=InCommon Server CA are presented to clients.
Certificate: Wireshark
- Wireshark TLSv1 Failure - Unknown CA
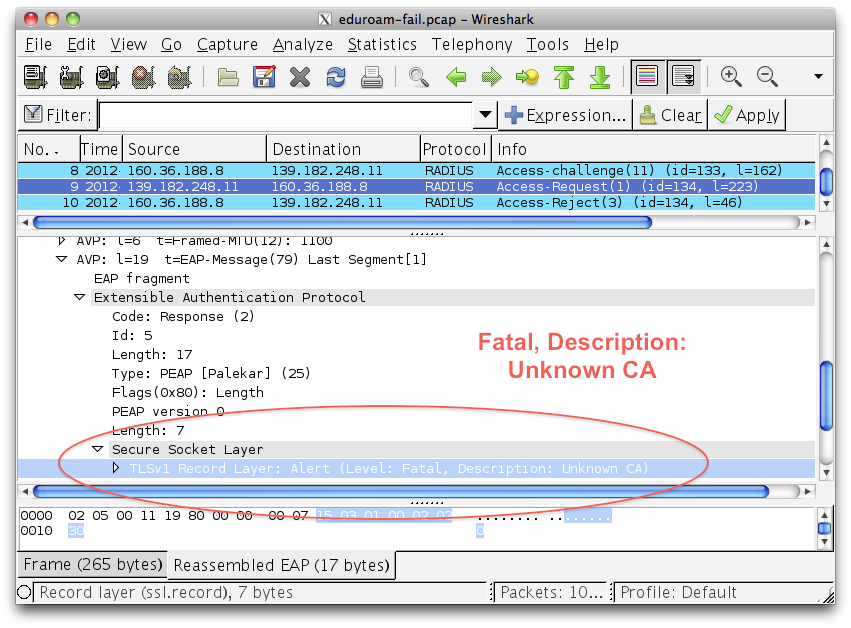
A Wireshark example of a client failing to connect because of a certificate issue. Just before the Access-Rejectdatagram, the RADIUS client forwards a "Unknown CA" alert.
Logging and Debugging
NPS logs rotate daily — they are noisy and get big quick. They are also forwarded to a syslog server using Snare Epilog for Windows
We wrote a tool to view NPS logs
We used tcpdump and Wireshark to debug Protected EAP termination and to ensure that the proper certificate chain was presented by our NPS server
We built the Linux eapol_test tool as suggested by the eduroamus.org debug page and added that Linux system to NPS as a RADIUS client
$ wget http://hostap.epitest.fi/releases/wpa_supplicant-1.0.tar.gz
$ tar zxvf wpa_supplicant-1.0.tar.gz
$ cd wpa_supplicat-1.0/wpa_supplicant
$ vi .config
$ make eapol_test
$ cat .config
CONFIG_IEEE8021X_EAPOL=y
CONFIG_EAP_MSCHAPV2=y
CONFIG_EAP_TLS=y
CONFIG_EAP_PEAP=y
CONFIG_EAP_TTLS=y
CONFIG_EAP_LEAP=y
CONFIG_IEEE8021X=y
We had help from Chad Bauer from eduroam-US with debugging connectivity to eduroam US Top Level and from Carl Oakes from CSU Sacramento with testing federation accounts.