Administrative Privileges Risks
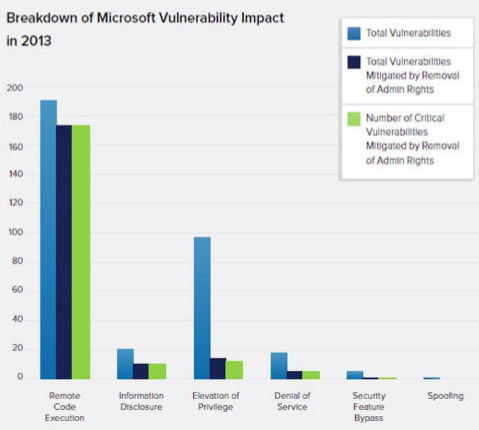
As much as 86% of critical vulnerabilities are mitigated by limiting administrative privileges. Critical vulnerabilities are those that are exploited to disclose personal information, destroy critical data, harm reputations, and give attackers a foot-hold to attack sensitive internal systems. These risks are mitigated by limiting the use of administrative privileges. As such, unrestricted use of administrative privileges unnecessarily increases risk and liability for the university.
Avecto 2013 Microsoft Vulnerabilities Study: Mitigating Risk by Removing User Privileges
Standard
Limiting administrative privileges complies to CSU Policy 8060.00 and CSUSB Access Control Standards: "All access privileges must be based on the required duties and responsibilities of each user or system." Recently, CSUSB went through a CSU Information Security audit. Finding #8 of audit 14-55 was in regard to administrative privileges on network connected Desktops/Laptops. The finding recommends CSUSB “eliminate administrative access to workstations unless it is specifically approved”.
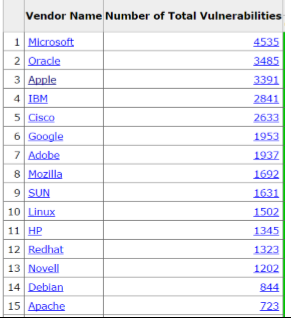
Apple and Linux Based Computer Vulnerabilities
All systems have some level of vulnerabilities, including Apple and Linux systems, the following is graphical list of the top 15 vendors sorted by total number vulnerabilities.
cvedetails.com vulnerability by vendor
Installing Software or Updates
Although administrative rights can be abused to bypass security controls and install unwanted software, they are often used to install and update legitimate software. However, CSUSB maintains infrastructure that allows managed computers to receive new software and updates without requiring administrative privileges. Managed desktop and laptop systems receive lists of “pushed” software. Efforts are made to do this offhours to avoid interrupting productivity. Software missing from the list can be added by request to the Technology Support Center, where it will be distributed and maintained on all relevant desktops. Requesting a technician to schedule a manual install or update for you is still an option, if necessary.
Exceptions
University employees who use systems that cannot be managed practically, such as computers used for research purposes, or who require extra-ordinary permission for their job duties, may request an exception to policy using the process.
Summary
Limiting Administrative Privileges: 1) Reduces risks to users and systems 2) Addresses Finding #8 in Audit 14-55 at CSUSB 3) Conforms to CSU Policy 4) Is a best practice and is generally not needed by users
Sources & References
Further reading on the topic and references for graphs are also available on the page CSUSB Administrative Privileges.
Sources and further reading
http://www.infoworld.com/article/3029400/security/security-flaws-not-so-critical-if-admin-rights-are-taken-away.htmlhttp://www.zdnet.com/admin-rights-key-to-mitigating-vulnerabilities-study-shows-7000026428/
http://www.sans.org/reading-room/whitepapers/bestprac/system-administrator-security-practices-657
http://technet.microsoft.com/en-us/magazine/2008.05.desktopfiles.aspx
http://www.eweek.com/c/a/Security/Is-System-Lockdown-the-Secret-Weapon/
http://technet.microsoft.com/en-us/library/bb456992.aspx#EJAA
Refrences
https://www.cvedetails.com/product/156/Apple-Mac-Os-X.html?vendor_id=49
https://www.avecto.com/resources/reports/2013-microsoft-vulnerabilities-report
http://www.iso.org/iso/home/store/catalogue_tc/catalogue_detail.htm?csnumber=54534